Table of Contents
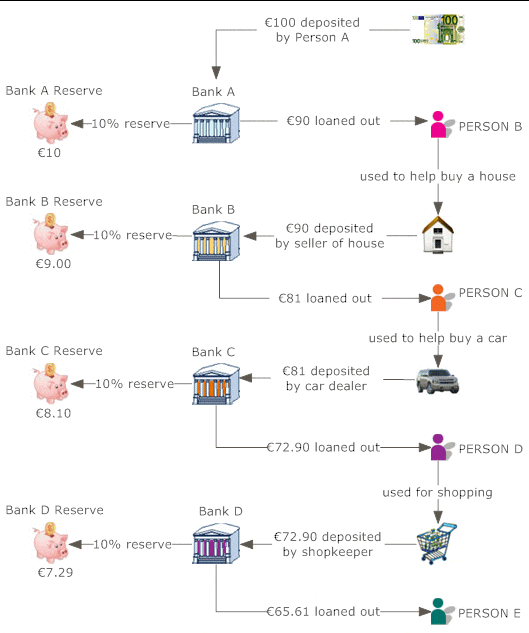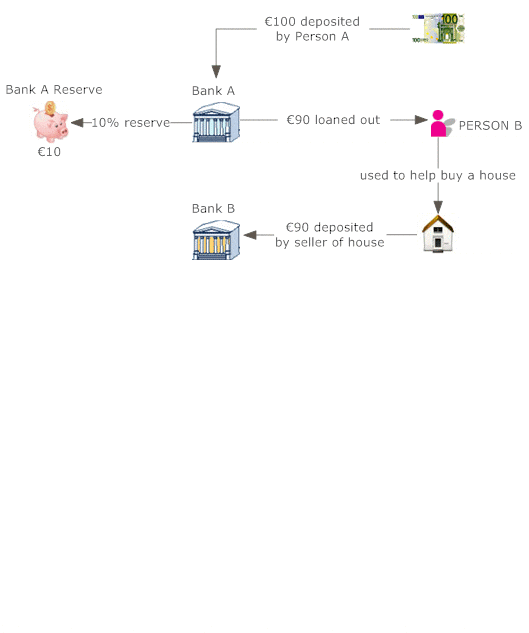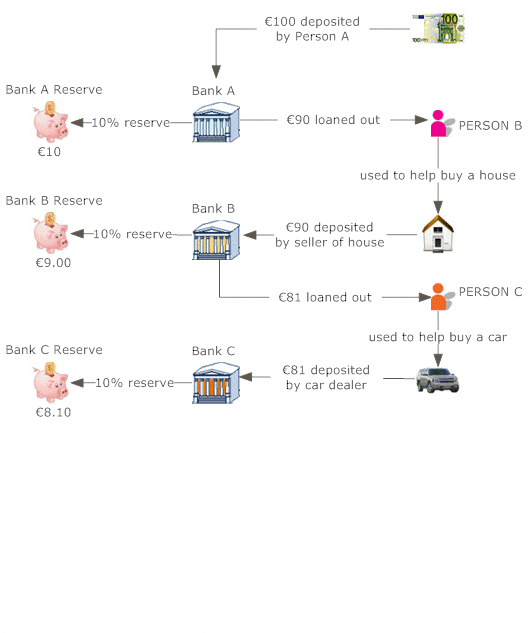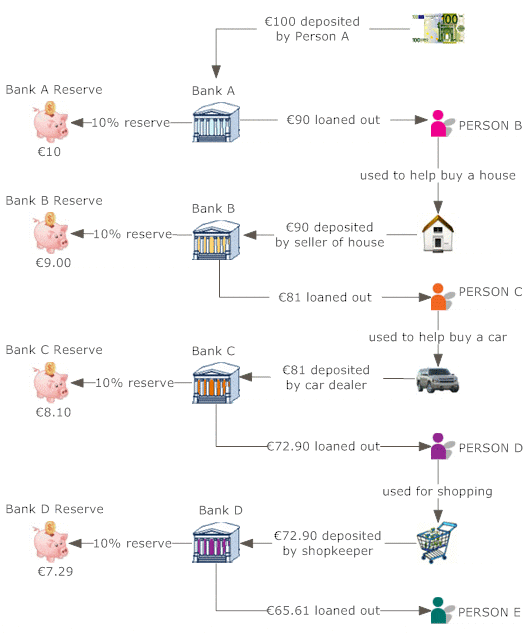
The money conversion cycle (CCC) is just one of numerous procedures of monitoring efficiency. It gauges exactly how quickly a firm can transform cash handy into much more cash on hand. The CCC does this by following the cash, or the capital expense, as it is first exchanged inventory and accounts payable (AP), via sales and accounts receivable (AR), and after that back into cash.
A is using a zero-day manipulate to trigger damage to or steal information from a system influenced by a susceptability. Software application commonly has security susceptabilities that cyberpunks can make use of to cause havoc. Software developers are always looking out for susceptabilities to "spot" that is, develop a solution that they launch in a brand-new update.
While the susceptability is still open, aggressors can compose and apply a code to take benefit of it. As soon as enemies recognize a zero-day susceptability, they require a way of reaching the at risk system.
The Main Principles Of Security Consultants
Protection susceptabilities are typically not found straight away. It can occasionally take days, weeks, or perhaps months before designers recognize the susceptability that brought about the assault. And even as soon as a zero-day spot is launched, not all customers are quick to apply it. Recently, hackers have been quicker at making use of vulnerabilities right after discovery.
: cyberpunks whose motivation is typically financial gain hackers motivated by a political or social reason that want the strikes to be noticeable to draw attention to their cause cyberpunks that snoop on business to get information about them countries or political actors spying on or attacking another nation's cyberinfrastructure A zero-day hack can exploit susceptabilities in a selection of systems, consisting of: As a result, there is a broad variety of potential targets: Individuals that utilize a prone system, such as an internet browser or operating system Hackers can make use of security susceptabilities to endanger devices and build huge botnets Individuals with access to beneficial company data, such as copyright Equipment devices, firmware, and the Web of Things Large organizations and companies Federal government companies Political targets and/or nationwide protection threats It's practical to believe in regards to targeted versus non-targeted zero-day assaults: Targeted zero-day assaults are executed versus possibly beneficial targets such as big organizations, federal government companies, or top-level individuals.
This website utilizes cookies to help personalise material, tailor your experience and to keep you logged in if you register. By proceeding to utilize this website, you are granting our usage of cookies.
The Buzz on Banking Security
Sixty days later is usually when a proof of principle emerges and by 120 days later, the vulnerability will certainly be consisted of in automated susceptability and exploitation devices.
Prior to that, I was just a UNIX admin. I was thinking of this concern a lot, and what occurred to me is that I don't understand also several individuals in infosec that picked infosec as a job. Most of individuals that I understand in this area didn't go to college to be infosec pros, it simply sort of occurred.
Are they interested in network safety and security or application protection? You can obtain by in IDS and firewall world and system patching without knowing any code; it's relatively automated things from the item side.
The Ultimate Guide To Banking Security
So with equipment, it's a lot various from the work you make with software protection. Infosec is a really large space, and you're going to have to pick your specific niche, since no one is mosting likely to be able to connect those spaces, at least effectively. Would you state hands-on experience is more essential that formal safety education and learning and certifications? The concern is are individuals being worked with right into access level safety and security settings right out of institution? I believe somewhat, however that's most likely still rather unusual.
There are some, however we're possibly speaking in the hundreds. I think the universities are simply now within the last 3-5 years getting masters in computer system protection scientific researches off the ground. There are not a lot of pupils in them. What do you assume is one of the most vital qualification to be effective in the safety area, despite an individual's history and experience level? The ones that can code almost always [fare] much better.

And if you can understand code, you have a much better possibility of being able to comprehend exactly how to scale your remedy. On the defense side, we're out-manned and outgunned continuously. It's "us" versus "them," and I don't understand the number of of "them," there are, yet there's going to be as well few of "us "whatsoever times.
Our Security Consultants Diaries
For instance, you can imagine Facebook, I'm unsure numerous safety individuals they have, butit's mosting likely to be a small fraction of a percent of their user base, so they're mosting likely to need to determine how to scale their services so they can protect all those customers.
The scientists noticed that without knowing a card number ahead of time, an enemy can introduce a Boolean-based SQL injection through this area. Nonetheless, the database responded with a 5 second delay when Boolean real statements (such as' or '1'='1) were offered, resulting in a time-based SQL injection vector. An aggressor can use this technique to brute-force inquiry the database, permitting details from easily accessible tables to be subjected.
While the information on this dental implant are limited right now, Odd, Work works with Windows Web server 2003 Enterprise approximately Windows XP Specialist. Some of the Windows exploits were even undetected on online data scanning service Virus, Total amount, Security Architect Kevin Beaumont confirmed by means of Twitter, which indicates that the devices have not been seen prior to.
Navigation
Latest Posts
Diy Plumbing close to Albuquerque
Should I Plumb My Own Home near me Albuquerque
Should I Plumb My Own Home close to Albuquerque